|
Malware Guide: Removal Tools < [6/7] >
Table of Contents
Introduction
Now that you have the knowledge on how to manually extricate malware from your system that you've identified, it is now time to put together an arsenal of tools that will do some of the leg work for you. My only warning is that you should not depend on these 100% as they often will not find everything, and sometimes they will cause other problems. The reason I explained the above topics is that you should be able to gain an intuition on how malware works, and from that you should be able to intelligently use the tools at your disposal.
You should be skeptical of most malware removal programs, because a lot of times they are malware in disguise. This is especially true for spyware / adware programs. You will think that you're installing a program that will provide assistance in removing pesky popups, but instead you just install more popup causing programs. The list of programs I provide below are trusted and reliable applications that have been time tested.
Return to top.
Ad-Aware [Lavasoft] - Spyware, Adware
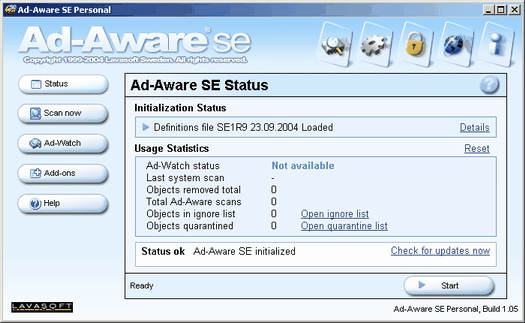 This program is most likely the most well known program for detecting and removing adware. It uses adware/spyware reference file definitions to detect unwanted files. It lets you update these through a button in the program. Then you can run a scan as you would in a virus scanner. After it finishes rummaging through your files it shows you a list of detected spyware/adware and lets you choose which to remove. The program itself is freeware for personal use so if you're a business you are supposed to buy it. There is also a professional version available that isn't free but offers additional features such as real-time scanning. This program is most likely the most well known program for detecting and removing adware. It uses adware/spyware reference file definitions to detect unwanted files. It lets you update these through a button in the program. Then you can run a scan as you would in a virus scanner. After it finishes rummaging through your files it shows you a list of detected spyware/adware and lets you choose which to remove. The program itself is freeware for personal use so if you're a business you are supposed to buy it. There is also a professional version available that isn't free but offers additional features such as real-time scanning.
The program has a very simple design, and anyone familiar with a virus scanner should be perfectly at home with this program. Once it is started you first need to make sure you have the latest definitions / reference file. This can be done from the main menu with the check for updates now button text. You will have to be connected to the Internet for this to work, but it will then download the latest comparison files from Lavasoft.
Then you need to use the main menu's scan now button. The default options should be just fine as I have never seen a reason to change them. For the power users though, you can configure Ad-Aware to some degree. When you tell it to the program will scour your computer for files that match up with its spyware / adware list. And once it has finished scanning it will then let you select the programs you want to remove. I normally right click and select all since I consider all spyware / adware to be junk, but it is possible that you have some program that requires an adware / spyware component to run, and you really want that attached program (such as KaZaA). In any event, once you tell it to fix the selected items it will run through the list you selected and remove them one by one in a very short period of time.
For the most part Ad-Aware runs very well, but it doesn't detect all spyware / adware, especially not the newest variants of some of the more insidious programs such as CoolWWWSearch, but it gets about 99% of it. It is also possible that some spyware / adware will detect if you run Ad-Aware, and may close it or slow it down. In situations such as this you will have to use another program, and I normally resort to Process Explorer so I can close down the offending processes before I run a scan with Ad-Aware and/or Spybot.
Return to top.
Spybot - Seek & Destroy [Safer-Networking] - Spyware, Adware
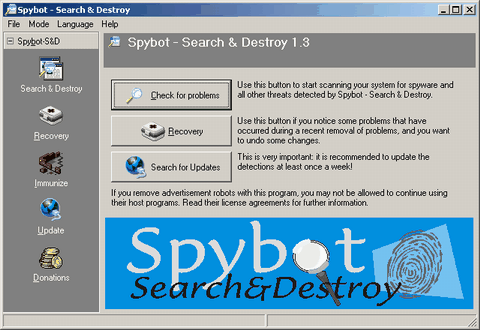 Spybot is the purely free alternate to Ad-Aware. The program behaves very similarly to Ad-Aware, but the program has two major differences. The first is that the program design is less clean looking. And the second is that it has many more advanced features, but you have to manually turn them on. But, it uses definition / reference files just like Ad-Aware, and it must be updated on a regular basis. Spybot is the purely free alternate to Ad-Aware. The program behaves very similarly to Ad-Aware, but the program has two major differences. The first is that the program design is less clean looking. And the second is that it has many more advanced features, but you have to manually turn them on. But, it uses definition / reference files just like Ad-Aware, and it must be updated on a regular basis.
When started for the first time the program will force you to update your definitions, but remember that after the fiirst time you should update the definitions manually anytime you wish to run a scan. From the main menu of the program, labeled Spybot-S&D, you can either search for updates or check for problems. Like I said before, you should update before you scan. You should also realize the button on the switchbar named update will also bring you to the update page. When you attempt to find updates it will connect to the Spybot server, so you'll need to be online, and it will present you with a list of updates. If any are available then you need to select the updates you want by checking the items to download, and then you need to use the download updates button.
Once updated you can use the check for problems button on the main menu, or you can use the search & destroy button on the side switchbar. When you tell it to search for problems it will begin scanning for objects it recognizes as spyware / adware. This process can take a few minutes, but I find the program is normally faster than Ad-Aware.
After the scan is complete you will be presented with a list of items it thinks you don't want. By default all the items should be selected. When you've verified the list then use the fix selected items button to get rid of them. It is possible that you may want to keep some of the items as some, typically free, programs come bundled with spyware / adware that they required installed in order for them to operate. So, if you clean out all spyware / adware then some of these programs may stop working, and you may need to reinstall them if this happens.
Overall I find that Spyware detects more spyware / adware than Ad-Aware, but that could easily change. But, don't let that detour you from using Ad-Aware. I find that by using Ad-Aware and Spybot, in conjunction, I can find all but a few different variants of spyware / adware. So, I suggest using them both. It is also possible that some programs may scan for the presence of Spybot and terminate it or slow it down. In situations such as this you will have to use another program, and I normally resort to Process Explorer so I can close down the offending processes before I run a scan with Ad-Aware and/or Spybot.
Return to top.
Virus Scanner [Symantec, Mcafee] - Worms, Viruses, Trojans
Most virus scanners the same and most people are familar with virus scanners. The two most common brands are Symantec and Mcafee. But, there are dozens of other virus scanners, some of which are even free. The truth is that they are all about the same, but I personally use Symantec Antivirus Corporate 9.
The most important part to using an antivirus program is to make sure the definitions are kept up-to-date. A virus scanner can only detect viruses that it has been updated to detect, so a virus scanner with definitions that are several months old does nothing but slow down your computer. The heuristic abilities of a virus scanner, which are the features of a virus scanner that can detect virus like patterns in a file, are fairly useless and find more false positives than real viruses.
Return to top.
CWShredder [Merijn.org] - Spyware, Adware
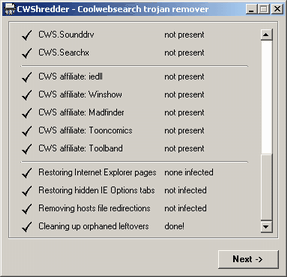 A horrible spyware / adware programs exists called CoolWWWSearch (CWS). The program employs very tricky techniques to install itself on your computer, and starts in exceptionally strange ways. The program also uses failsafes to detect when it's being removed, so it is very hard to manually uninstall. But, what is worse is the programmers for CWS write a new version almost weekly. To combat this the smart guy at Merijn wrote CWShredder that automatically removes all entries of CWS, and he came out with versions as soon as he figured out how to remove the latest variant of the program. Sadly, he got sick of the constant battle, so he gave up the project. But, the program still removes most CWS installations, so the program is still very useful. A horrible spyware / adware programs exists called CoolWWWSearch (CWS). The program employs very tricky techniques to install itself on your computer, and starts in exceptionally strange ways. The program also uses failsafes to detect when it's being removed, so it is very hard to manually uninstall. But, what is worse is the programmers for CWS write a new version almost weekly. To combat this the smart guy at Merijn wrote CWShredder that automatically removes all entries of CWS, and he came out with versions as soon as he figured out how to remove the latest variant of the program. Sadly, he got sick of the constant battle, so he gave up the project. But, the program still removes most CWS installations, so the program is still very useful.
Using this program is simple. When you run it the main menu gives you a bit of information about itself. But, the button we're concerned with is the fix button. Close all Internet Explorer windows first, and then click on fix. It shouldn't take long to scan, but it will check for all possible infection points for all the known variants of CWS, as of the latest version of the program. If it finds one then it removes it, and it says removed in the second column besides the name of that variant. If it doesn't find it, then it says not present. That's all there is to this program, but I have found it exceptionally useful none-the-less.
You can also download CWShredder this from my website [cwshredder.exe], however you should be aware that my version may not be up-to-date. So unless you have malware blocking you from visiting Merijn's site then I suggest getting it the primary source.
Return to top.
Process Explorer [Sysinternals] - Spyware, Adware, Worms, Viruses, Trojans
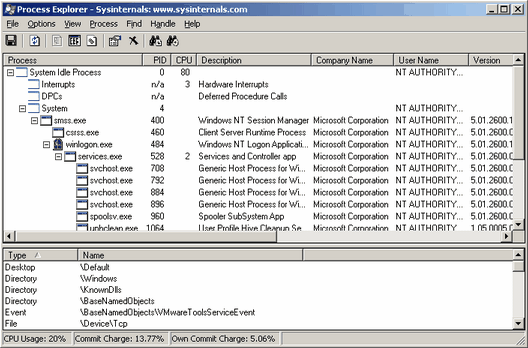 One of my favorite tools for locating malware is process explorer. This program is basically a beefier version of the Windows task manager, but it provides functionality that task manager should, but does not. The concept here is to use this to locate rogue processes, because all programs, malware or not, has to be running. It should be noted that some spyware/adware run as a DLL instead of as an EXE, so the culpret may be elsewhere. One of my favorite tools for locating malware is process explorer. This program is basically a beefier version of the Windows task manager, but it provides functionality that task manager should, but does not. The concept here is to use this to locate rogue processes, because all programs, malware or not, has to be running. It should be noted that some spyware/adware run as a DLL instead of as an EXE, so the culpret may be elsewhere.
To use this program first run it. Then look for suspicious filenames. It helps a lot to be familiar with system files on a clean system. A lot of malware will disguise themselves as system files, but often they'll misspell their names. Using process explorer you can use other tricks to locate malware.
The program displays the heirarchy of programs. So, if a program is started by the Windows explorer, then it falls under it. And if that program starts another program, then it falls under that. This provides very helpful information because it allows you to distinguish system files from normal programs. So any program under Explorer is a normal program that is in no way required for proper system functionality. This means you could safely terminate all of those and you wouldn't crash the system. So for those it is better to be suspcious then not to be. For the programs under services, those are system services that could be required for system use.
The field for company name is very useful. Generally, most good programs display their company name, but most malware does not. This is not always the case, but usually you can be fairly sure a program is made by Microsoft if it says Microsoft Corporation in that field. This is very helpful for identifying fake svchost.exe, csrss.exe, winlogon.exe, explorer.exe, services.exe, lsass.exe, iexplore.exe, spoolsv.exe, alg.exe, and smss.exe processes. If they don't have Microsoft Corporation in the company name field, then they're almost positively pretenders.
Often viruses, worms and trojans will consume a good deal of resources. This means that the CPU field will display a rather high number, since it displays the percentage of the CPU that process is using, and may consume a great deal of memory (working set and/or virtual size). Most programs should use less than 1% of CPU time if they're not doing anything you would expect to be CPU intensive, but lots of malware is active all the time, and that's why it affects your computer's performance so much.
If you double click on a process then you will be presented with a dialog with more information on that process. You can see the path it is located in, service information (if it is a service), performance data, etc. If you want to terminate a process then use the kill process button.
If a file is suspicious then look up where the file is located, take note of it, and terminate the process. If you lose system functionality or the computer crashes, then you terminated something you should not have (and you may need to reboot). If your problems go away then you found the malware and you should rename that file, or delete it if you are sure you won't need it again. Some malware may restart themselves when terminated, so you may have to remove the file from within safe mode.
You can also download Process Explorer from my website [procexp.exe], however you should be aware that my version may not be up-to-date. So unless you have malware blocking you from visiting Sysinternal's site (which isn't likely) then I suggest getting it the primary source. Return to top.
Hijackthis [Merijn.org] - Spyware, Adware
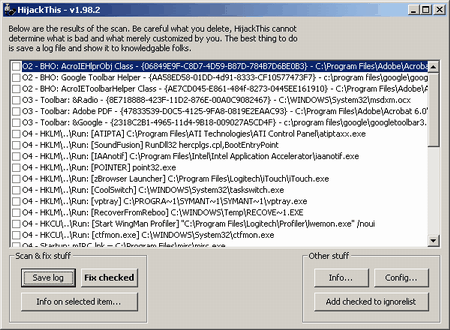 A useful program for locating and removing browser plugins is Hijack this. Many malware applications will install themselves as add-ins to Internet Explorer, and this program will present you with a list of all add-ins to Internet Explorer. If you are having popups appear only when Internet Explorer visits a website, or if your homepage / startpage keeps being changed, then you most likely have malware add-ins. A useful program for locating and removing browser plugins is Hijack this. Many malware applications will install themselves as add-ins to Internet Explorer, and this program will present you with a list of all add-ins to Internet Explorer. If you are having popups appear only when Internet Explorer visits a website, or if your homepage / startpage keeps being changed, then you most likely have malware add-ins.
The program is very simple and consists of only a single window. When started the main window pane of the program will be empty, and a button labeled Scan in the bottom left should be used to get started. The scan should only take a second. Technically what it does is it looks up in the registry the browser helper object (BHO) files that are associated as plugins to Internet Explorer, and cross references the data it retrieves to obtain a slightly more meaningful display, because BHOs normally only look like a string of numbers and letters. So the display you get is a list of all the plugins for Internet Explorer. It also displays a few other startup items that can be found in other registry entries to be a bit more of a help. But, generally I remove those entries either using Internet Explorer or MSConfig.
Your job then is to identify and select all the items you wish to remove from Internet Explorer. This can be a bit tricky because the items have fairly cryptic filenames, so you can't always easily identify the BHOs. If you are unsure about a particular entry then you should look it up on Google. But, you should understand that you are safe to remove all of these, and Internet Explorer will still function properly. The only thing you could end up disabling are your plugins, and that could range from viewing Flash to Shockwave to Windows Media files in Internet Explorer, but those are easy to reinstall if they stop functioning properly. You should also pay special attention to the browser start page entries, because those are often changed by spyware / adware.
When you are done selecting any suspicious items, then first make sure that all Internet Explorer windows are closed. Then use the Fix checked button and it will remove all the entries that you had selected. This should work for most malware that integrates to Internet Explorer, but some malware can be especially insidious and may reintegrated if given the chance. By this I mean that sometimes malware has rogue processes running that will reinsert themselves after being removed, so you may have to take more extreme measures to get rid of them then, such as deleting the program files from within safe mode. You can also download Hijackthis this from my website [hijackthis.exe], however you should be aware that my version may not be up-to-date. So unless you have malware blocking you from visiting Merijn's site then I suggest getting it the primary source. Return to top.
System Configuration Utility (MSConfig) - Spyware, Adware, Worms, Viruses, Trojans
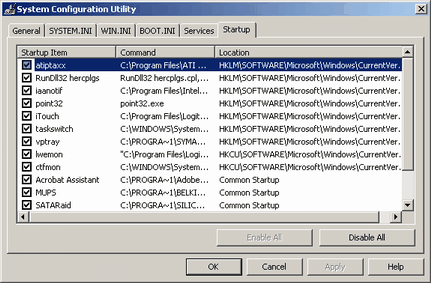 This is a tool that comes installed with Windows XP (and most likely Longhorn). It does not come with Windows 2000, but if you're not fortunate enough to have XP and have 2000 instead then you can grab MSConfig from an XP computer and use it (although I imagine this is in theory breaking the XP license). It can be a very useful tool for removing malware from your system, but it isn't a perfect tool. Traditionally the program was meant to diagnose booting problems, but it works well for finding and disabling malware. To run it simply click on your start menu, click on run and type in msconfig, then hit okay. This is a tool that comes installed with Windows XP (and most likely Longhorn). It does not come with Windows 2000, but if you're not fortunate enough to have XP and have 2000 instead then you can grab MSConfig from an XP computer and use it (although I imagine this is in theory breaking the XP license). It can be a very useful tool for removing malware from your system, but it isn't a perfect tool. Traditionally the program was meant to diagnose booting problems, but it works well for finding and disabling malware. To run it simply click on your start menu, click on run and type in msconfig, then hit okay.
The general tab of the program allows you to optionally select which items you wish to load on startup. The general idea here is that you can turn off features that could be making your computer unstable, and basically restrict your computer to a non-hardware accelerated safe mode, even though you're in normal mode. This tab isn't very helpful in our situation, or at least it would be too complicated to use in this situation.
The WIN.INI tab could be used to disable the INI startup location for run=. However, I would suggest reading the detection and removal chapter for editing the ini manually.
The services tab is an alternate way to edit system services. I generally recommend using the services.msc console because it provides much more information and isn't as risky to use. Whereas it is possible to disable all services using MSConfig, which would make your computer unbootable.
The startup tab is a great way to view the startup items on the computer instead of tromping around in the registry and in the start menu. It doesn't allow you to edit items though, so that does limit you to a good degree. But, it at least lets you disable the startup items.
Return to top.
Add / Remove Programs [Appwiz.cpl] - Adware, Spyware
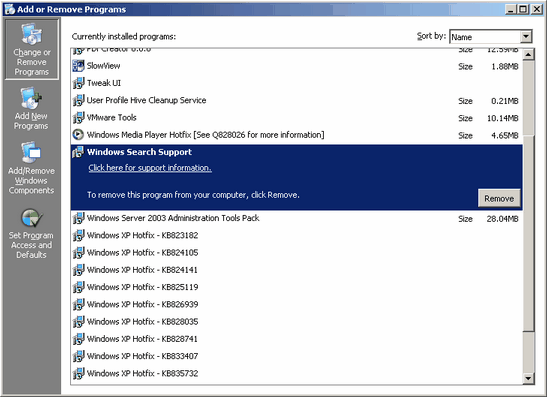 The most obvious place to remove adware or spyware is through the add / remove programs menu in the control panel. In fact, this place is such an obvious place to look that it is often overlooked. People consider spyware and aware to be so insidious that they forget to remember that they're just normal programs. The point here to understand is that only a fraction of adware or spyware is so bad that it can't be uninstalled in traditional manners. When you attempt to uninstall them they may make you jump through a few hoops, but they generally all let you uninstall them. Try this before using a program like Spybot or Ad-Aware, because this guarantees they will be cleanly removed. The most obvious place to remove adware or spyware is through the add / remove programs menu in the control panel. In fact, this place is such an obvious place to look that it is often overlooked. People consider spyware and aware to be so insidious that they forget to remember that they're just normal programs. The point here to understand is that only a fraction of adware or spyware is so bad that it can't be uninstalled in traditional manners. When you attempt to uninstall them they may make you jump through a few hoops, but they generally all let you uninstall them. Try this before using a program like Spybot or Ad-Aware, because this guarantees they will be cleanly removed.
They employ a few tricks to hide. They add themselves to your uninstall list to maintain a legitimate front, but they try to blend in with other normal applications so you don't think of removing them. So they'll often have proactive names that sound useful, or they'll sound like a system file. Scan through the list carefully, and if you notice something that looks suspicious then either look it up to see if it is a useful program or attempt to remove it. Often spyware or adware that is removable will become apparent when you are presented with the dialog box that begs you not to uninstall the program because it provides so many useful features and how they need to feed their 20 children and their mother dying of cancer, or some other garbage. Sometimes you will need to be online to uninstall them, and sometimes you will need to fill out a short questionaire that they require you to fill out, but don't bother to give them real answers.
Return to top.
Symantec Removal Tools [Symantec] - Worms, Viruses, Trojans
These are free standalone programs that Symantec (developer of Symantec Antivirus / Norton Antivirus) releases to destroy the most destructive and the most common viruses, worms and trojans. They have quite a few of these programs and they will get rid of such common malware programs as MSBlast, Gaobot, Sasser, Codered, etc. Most of them are extremely easy to use and they let you know if they found anything after they have removed them.
Return to top.
TCPView [Sysinternals] - Worms, Trojans, Spyware
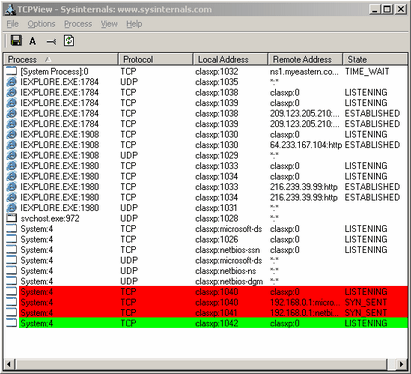 TCPView is an extremely helpful tool when it comes to locating "noisy" processes. This program is basically a more advanced and graphical version of the command-line tool netstat. It will show you what ports and tunnels are open on your computer, what the local and destination addresses are, and it will show which program is handling it. If you're not familiar with what a port is then I suggest reading my network guide. Using this program is a bit more advanced than most, but the general idea is that if a program has a lot of connections open then it's a very "noisy" program, which usually means it is either a P2P program or it's a worm scanning for vulnerable computers to infect. TCPView is an extremely helpful tool when it comes to locating "noisy" processes. This program is basically a more advanced and graphical version of the command-line tool netstat. It will show you what ports and tunnels are open on your computer, what the local and destination addresses are, and it will show which program is handling it. If you're not familiar with what a port is then I suggest reading my network guide. Using this program is a bit more advanced than most, but the general idea is that if a program has a lot of connections open then it's a very "noisy" program, which usually means it is either a P2P program or it's a worm scanning for vulnerable computers to infect.
When executed you will see a list of current connections and listening connections. The current connections are ones listed with the state of established, and listening are listed as listening. A established connection means there is an active data tunnel that is accepted at both ends. A listening state means the connection is waiting for a connection to be made. A connection with the state of syn_sent represents a request. And the color red means a connection that has been recently terminated and the color green represents a new connection. This program shows you the program making the connection and that's followed by a colon and the process ID (PID), which is a unique identifier for the process. System processes are designated by system or [system process]. It also tells you the local computer and port, as well as the remote endpoint IP and port. Plus it specifies the protocol type. It should be noted that many UDP connections is usually considered bad as they're typically used in network attacks, which could mean your computer is hacked or wormed.
You can also download TCPView from my website [tcpview.exe], however you should be aware that my version may not be up-to-date. So unless you have malware blocking you from visiting Sysinternal's site (which isn't likely) then I suggest getting it the primary source.
Return to top.
Netstat [netstat.exe] - Worms, Trojans, Spyware
Netstat is a program that comes with all Windows versions and can be used in the same ways that TCPView can be. However, netstat is a command line program so it isn't as attractive and it is harder to use and make sense of. TCPView also reveals more information because it does such things as reveal the process name, instead of just the PID (Windows XP) or nothing at all (before XP). For this reason I suggest using TCPView and only advanced users should worry about netstat.
Return to top.
Filemon [Sysinternals] - Spyware, Adware, Worms, Viruses, Trojans
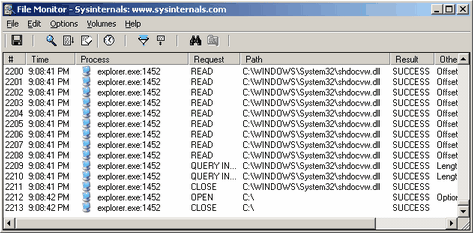 One of the tricky parts about removing malware is finding all of its pieces. This is not normally required, but sometimes it feels better to get rid of as much of it as possible. This is especially the case with worms, trojans, and viruses because they often have multiple components, such as included rootkits, that are sometimes not detected by virus scanners. And those components are just as dangerous as the other components. One of the tricky parts about removing malware is finding all of its pieces. This is not normally required, but sometimes it feels better to get rid of as much of it as possible. This is especially the case with worms, trojans, and viruses because they often have multiple components, such as included rootkits, that are sometimes not detected by virus scanners. And those components are just as dangerous as the other components.
Filemon is a program that monitors file activity. With it you can see which programs are accessing what files and how they manipulated the file. It even goes as far to tell you what data it accessed to / from the file. It monitors reads, writes, opening a file handle, and closing a file handle. It also tells you if it succeeded or not, because a file could be locked to another process or that program may lack access to a file and receive a failure.
The useful part of this is that you could watch a particular program and watch which files it accesses. This way you could locate all of the secondary components of the malware, such as DLL files and configuration files. It can also be used to watch a root kit to monitor how it installs itself on a target machine. These are complex methods though, and I suggest only bothering if you have a reason to.
You can also download Filemon from my website [filemon.exe], however you should be aware that my version may not be up-to-date. So unless you have malware blocking you from visiting Sysinternal's site (which isn't likely) then I suggest getting it the primary source.
Return to top.
Regmon [Sysinternals] - Spyware, Adware, Worms, Viruses, Trojans
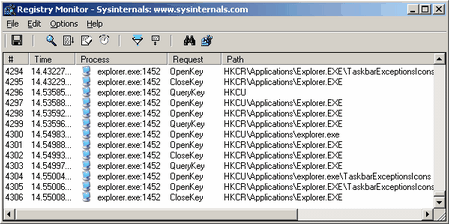 Normally a spyware or adware program, and even worms or trojans, will access the registry to store settings. These could be settings such as the malware version, or that it has completed a particular task, or that it has decided on a fate for the computer, such as carrier rather than target. Whatever the case, it is often comforting to locate these types of registry entries and remove them. Normally a spyware or adware program, and even worms or trojans, will access the registry to store settings. These could be settings such as the malware version, or that it has completed a particular task, or that it has decided on a fate for the computer, such as carrier rather than target. Whatever the case, it is often comforting to locate these types of registry entries and remove them.
Regmon is a program that monitors registry activity. If you are not familar with the registry then you may want to read my Windows Components guide to better understand how important it is. With this program you can see when a program opens a key, closes a key, reads a key or sets a key. With it you can see which programs are accessing what registry entriesand how they manipulated the values or keys. You can even see which data is written to values, which could provide a great deal of insight into a malware application.
The useful part of this is that you could watch a particular program and watch which part of the registry it accesses. This way you could locate all of the secondary components of the malware. It can also be used to watch a root kit to monitor how it installs itself on a target machine. These are complex methods though, and I suggest only bothering if you have a reason to.
You can also download Regmon from my website [regmon.exe], however you should be aware that my version may not be up-to-date. So unless you have malware blocking you from visiting Sysinternal's site (which isn't likely) then I suggest getting it the primary source.
Return to top.
|