|
|
Components Guide: Access Control Lists
There are several things that make Windows NT4, 2000, XP and Longhorn different than Windows 95, 98 and Me, but access control lists (ACL) are some of the biggest differences. These lists also differentiate Windows NT based operating systems from Unix based operating systems like Linux, FreeBSD, HP-UX, Tru64, OS X, and many others, although it is possible to force ACLs into them with some degree of incompatible success. The concept behind an ACL is that it allows an object, whether that be a printer, file or something else, specific rights to another object, through user and group permissions. This works well in a local system so you can limit your kids, so they couldn't, as an example, install AIM to chat when they're being punished, or extremely well in a network where you want a group of users to be able to print to a network printer, but you don't want another group to be able to. So the concept of an ACL is to limit access to those authorized to. They are very powerful, but they could also be considered fairly complex. But, the access control lists in Windows allow for very granular control, especially on the file level, which makes Windows an excellent multi-user workstation and server. Access control lists can also be used to monitor the access of an object, so, for example, you could be notified if someone accesses a specific file.
Inheritance
When permissions are applied to an object that has subobjects the typical behavior is for the subobjects to inherit the properties of the object, although this varies from ACL implementation to ACL implementation. In these situations the object is called the parent object, and the subobjects are called child objects. These permissions are directly inherited to the child objects from the parent, if they're of similar types, but for objects that differ these permissions are translated to properties that are as similar as possible. For example, if you applied a list property to a folder, then this would be interpreted on a file as the ability to read the contents of the file.
Children don't always need to inherit the properties from the parent. In all access control list enabled contexts that have inheritance you can choose if you wish to inherit those properties or not. And usually you are able to append permissions to the inherited list, but this only allows you to add permissions and not remove them, unless you do it through a deny, which is not usually recommended. The importance of inheritance is that it allows for low maintenance. You wouldn't want to have to set permissions on every subfolder, so you want the permissions to follow through until you wish to change them at some lower level.
Return to top.
Ownership
Besides a list of users and groups that have access to an object, there is another property that is applied to every object. This property is called the owner. An object is assigned an owner when it is created by a user, or it can be manually assigned. The ability to usurp control of an object is performed through a take ownership permission, and this allows the user with that control to apply themselves as the owner of an object, which gives them full control of it. And in the local security policy on the computer there is an assigned list of users that can take ownership of any files on the system/network.
Return to top.
Types
There are two types of access control lists. The first is called a discretionary access control list (DACL) and the second is called a system access control list (SACL). The DACL represents the permissions aspect of access control lists, while the SACL represents the auditing aspect of them. So the DACL properties allow or limit access to an object, where as the SACL monitors and logs access according to its properties.
Return to top.
Composition
Every access control list contains a list of access control entries (ACE). An entry is applied for every user or group that has permissions applied. Each ACE comprises of a security identifier (SID) that represents the internal name for a user or group. This SID is applied to a user or group at creation, and follows through until that user or group is deleted. This allows the user or group to be renamed while leaving the pointers intact. These ACEs also contain a list of permissions that specify the access rights to the object. These represent permissions such as delete, list or edit. They also contain a flag if the object is inheriting permissions from the parent object. And it also contains a flag that indicates whether it is a allow or deny ace.
Return to top.
Master File Table (MFT)
The access control lists are physically stored in the master file table (MFT) instead of being stored in the file itself. However, NTFS employs a technique of separation to speed up access times on files. So, if the attribute data for a file (including folders) is too large then it places the data in a different location than the rest of the MFT data, and places a forwarding address in the MFT. The MFT is stored at the beginning of a drive and for Windows XP it uses, by default, up to 12.5% of the drive. If the MFT grows beyond its limitation then the data is segmented and a speed loss incurs. However, this will rarely happen unless you have a lot of small files with lots of attributes.
Return to top.
ACL Configuration
It is similar to configure the access control lists on files for all versions of Windows. When you right click any file and select properties there will be a security tab that allows you to apply permissions to users and groups, but it looks slightly different for Windows NT4, Windows 2000 and Windows XP. From this view you cannot set very advanced options, but you can set typical access control options. So you can add a user or a group, and then set template permissions on the file/folder object. The permissions should be fairly understandable, but it should be noted that folders and files use the same access control options, but they mean different things. So if you look at a folder then it will list the option for read, whereas for a folder it would say list folder contents. These are parallel ideas, but applied differently because of their context.
In Windows 2000 and Windows XP you can also use the advanced button, which gives you much more granular control over the control lists. From here you can set the inheritability of the permissions, plus you can set around 13 different permissions. The previous permission types really just set these in template configurations, but you can also specify exactly the access type you want for a particular user or group. Using this you can configure very complicated control lists.
Return to top.
NT4 Differences
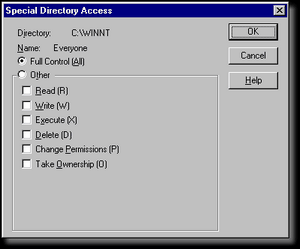 Windows NT4 is a much simplier operating system than Windows 2000, XP or the upcoming codenamed Longhorn. And this applies to the file system as well. Windows NT4 supports security descriptors like its more mature brothers, but it lacks in several areas. It should be noted that while the system appears less robust it has the underlying technology, but it doesn't allow you to use them. In order words, the file system supports more advanced settings but you cannot see or edit them. Windows NT4 is a much simplier operating system than Windows 2000, XP or the upcoming codenamed Longhorn. And this applies to the file system as well. Windows NT4 supports security descriptors like its more mature brothers, but it lacks in several areas. It should be noted that while the system appears less robust it has the underlying technology, but it doesn't allow you to use them. In order words, the file system supports more advanced settings but you cannot see or edit them.
In Windows NT4 you cannot set deny entries like you can in newer versions of Windows. As you can see from the permission list, you can only configure the template configuration types, which gives you a lot less control. Also, you can't set the inheritability of the permissions. This limits what you can do by a great deal because the files obtain the permissions explicitly from the folders, unless you explicitly alter the permissions on a file. In fact, the advanced tab that exists in newer versions of Windows does not exist in Windows NT4. So, in order to set auditing and ownership settings you will need to use the dialog previous to the permissions.
Luckily there are few people left using NT4. If you are still using it then you really may want to consider upgrading to Windows XP, for this reason as well as many others.
Return to top.
|
|