|
|
Malware Guide: Infection Methods < [3/7] >
Table of Contents
Introduction
Malware can be very insidious, and the ways they get onto your computer varies a great deal. I will try to outline the various methods that malware can infect your computer. One thing you should be aware of is that these are the current and common ways, and that malware creators are always trying new tricks to take advantage of your computer. Because of this you can't solely rely on this information, but hopefully it will give you an intuition that helps you understand ways they do get on your computer. If there's one thing you should know about malware is that they're in no way magical, they have to abide by the same rules as any other program, whether it be through function or flaw.
Return to top.
Bundled Malware
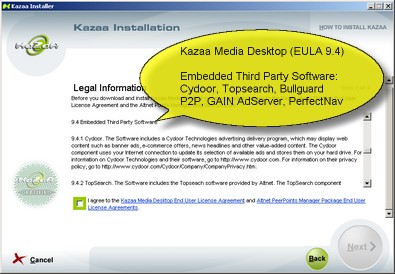 The first way I will discuss is through the malware being bundled within another program. Normally the programs that include malware are freeware programs, and the programs that include the worse type of malware can't even be paid for. Beware programs that offer something for nothing, especially if the author doesn't even accept donations. The programs that you shouldn't fear as much are the programs that appear as fairly legitimate shareware. These generally look visually professional, have a useful purpose beyond just changing your desktop's wallpaper, are not in the gray area of legality such as warez distribution applications, and you can actually understand their business model. Of course, some programs are actually free and the author is just being nice. But, you should always be cautious. Chances are if you get the program from a reputable site such as download.com then you can feel sure it won't have any viruses, worms or trojans, but it may contain some form of spyware or adware that is at worst annoying. Often these are noted on the information pages of the sites that distribute them, and a warning is often given in the End-User License Agreement (EULA) of the program on installation. If a program seems to be good to be true then do a little research on it before installing it. If you find it has malware, then consider what you're willing to sacrifice for that program. For example, just because a program spies on you does not mean it's not worth it. The first way I will discuss is through the malware being bundled within another program. Normally the programs that include malware are freeware programs, and the programs that include the worse type of malware can't even be paid for. Beware programs that offer something for nothing, especially if the author doesn't even accept donations. The programs that you shouldn't fear as much are the programs that appear as fairly legitimate shareware. These generally look visually professional, have a useful purpose beyond just changing your desktop's wallpaper, are not in the gray area of legality such as warez distribution applications, and you can actually understand their business model. Of course, some programs are actually free and the author is just being nice. But, you should always be cautious. Chances are if you get the program from a reputable site such as download.com then you can feel sure it won't have any viruses, worms or trojans, but it may contain some form of spyware or adware that is at worst annoying. Often these are noted on the information pages of the sites that distribute them, and a warning is often given in the End-User License Agreement (EULA) of the program on installation. If a program seems to be good to be true then do a little research on it before installing it. If you find it has malware, then consider what you're willing to sacrifice for that program. For example, just because a program spies on you does not mean it's not worth it.
Return to top.
Install on Demand
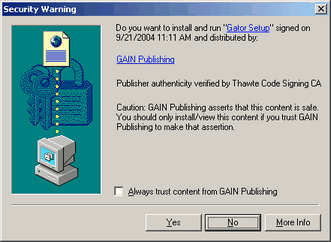 The second way malware commonly gets delivered is from Internet Explorer install on demand. When viewing web sites in Internet Explorer a web page can request to install an application on your computer. The user visiting the site will be presented with a dialog that asks if they would like to install the application that the site wishes them to install. It will normally tell you the name of the company or the program to be installed, but very little other information. You will have three choices of yes, no and more info. Normally a user will not even bother to read this popup as the security warning it claims to be, but rather click on yes blindly because they just want the web site they're visiting to load. Telling one of these dialogs yes will cause Internet Explorer to download the associated program and then install it. It should be noted that all programs that wish to install on demand (as this feature is called) are not malware, and many are quite useful and desired. An example of a program you wouldn't mind receiving like this is Flash, which is a program that allows you to watch animated videos on the web through a vector based language. The second way malware commonly gets delivered is from Internet Explorer install on demand. When viewing web sites in Internet Explorer a web page can request to install an application on your computer. The user visiting the site will be presented with a dialog that asks if they would like to install the application that the site wishes them to install. It will normally tell you the name of the company or the program to be installed, but very little other information. You will have three choices of yes, no and more info. Normally a user will not even bother to read this popup as the security warning it claims to be, but rather click on yes blindly because they just want the web site they're visiting to load. Telling one of these dialogs yes will cause Internet Explorer to download the associated program and then install it. It should be noted that all programs that wish to install on demand (as this feature is called) are not malware, and many are quite useful and desired. An example of a program you wouldn't mind receiving like this is Flash, which is a program that allows you to watch animated videos on the web through a vector based language.
For this reason you should be careful when you see one of these dialogs. Normally the program it links to will be spyware or adware, but it also has the ability to install a virus or such, and you would only have yourself to blame for this. To safeguard from this only install programs with this feature from web sites that you explicitly trust, or applications that you recognize. If you are not sure what the company is (like in that picture it is GAIN Publishing, an adware/spyware distributor) then research it a bit before answering. Also, if you cannot trust yourself to always do this or if someone uses your computer that you can't trust to do this (such as a teenage girl that installs every chat client under the sun on your computer) then you can disable this feature in the Internet Explorer options (tools, Internet options, under the advanced tab, enable install on demand (other)). Just remember to be skeptical of installs like the above one. It's good to be a bit paranoid.
Return to top.
Email Attachments
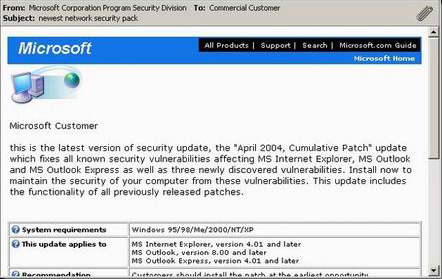 The third common way you can get infected from malware is from an email attachment. Normally the type of malware you get from email attachments are the on the bad side of the spectrum, and the vast majority of these are worms. This means you should be especially careful with email attachments. The creator of the email or email template will make a decent effort at the presentation of the email, but you can usually count on them being sloppy in some respect. As you can see from the picture on the left the email appears, at first glance, to be an email from Microsoft. A file is attached to this email called Installation28.exe, which is a name you could expect from a patch. Of course, if you are familiar with Microsoft you will know that they never send out patches by email, that their naming scheme involves the knowledge base article reference number and that the file size of this patch (104kB) is too small for any type of cumulative patch that it claims to be. To fool you the email has links back to Microsoft's web site and even links you to the Microsoft contact page if you have any questions, plus it has the Microsoft header and footer. The third common way you can get infected from malware is from an email attachment. Normally the type of malware you get from email attachments are the on the bad side of the spectrum, and the vast majority of these are worms. This means you should be especially careful with email attachments. The creator of the email or email template will make a decent effort at the presentation of the email, but you can usually count on them being sloppy in some respect. As you can see from the picture on the left the email appears, at first glance, to be an email from Microsoft. A file is attached to this email called Installation28.exe, which is a name you could expect from a patch. Of course, if you are familiar with Microsoft you will know that they never send out patches by email, that their naming scheme involves the knowledge base article reference number and that the file size of this patch (104kB) is too small for any type of cumulative patch that it claims to be. To fool you the email has links back to Microsoft's web site and even links you to the Microsoft contact page if you have any questions, plus it has the Microsoft header and footer.
So, how could a normal user tell the difference? Well that requires a bit of deduction. First of all the reply to email address is ngrmsafc@updates.com, which is definitely not a Microsoft email address and the userid (the first part of an email address, the part before the @ is called the userid and the second part is called the domain) definitely looks randomly generated. Second, the email has tons of grammatical mistakes such as the lack of a comma after Microsoft Customer, or the fact that the first sentence isn't capitalized. And we would hope that a company as large as Microsoft could afford to pay their employees to correct their grammar and spelling. If you are unsure of emails such as these then research it a bit to see if it follows any current trends of malware distribution, or in this case you could go directly to the Microsoft page and see if you can find this update under the same credentials and file size. In case you're wondering this was indeed a worm by the Symantec name of W32.Swen.A@MM. If this should teach you anything it is that under normal circumstances you should avoid running email attachments. You can't even trust friends or reputable companies because if a worm infects someone you know that worm could scan their address book and it may appear as if it came from them, when really it arrived from a mass mailing worm. However, if they are pictures, text or movie files then you can feel pretty sure they are safe, as long as their extensions are .JPG or .GIF or .BMP (or other images) and they are not .EXE or .COM or .JS (or other executable or script files). Do note that Windows sometimes hides the extensions of some files, and a file called pictures.jpg may really be pictures.jpg.exe and the last extension makes the file an executable and the .jpg is just part of the name. It should also be noted that images, movies, sound files, etc. can carry a malware payload if you are not patched.
Return to top.
Internet Hyperlink
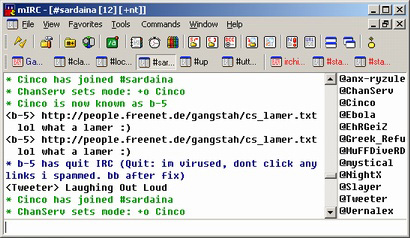 The fourth common way to be infected is by clicking on a link that directs you to malware. The link could either run a program and install the malware, or make use of a vulnerability that allows it to execute itself. This problem exists because the links often come from people you know and trust, and the links are often disguised with something to convince you it's harmless. All the instant messaging programs have had this problem such as AIM or Yahoo, but most of these trojans / worms occur on Internet Relay Chat (IRC). Due to the scripting engine of mIRC there are IRC trojans that take on worm like behaviors through macro virus like scripts. This allows the malware to take control of your chat client and then tell people to click on a link or such. Related to this problem, often the trojans will begin to send infected files to people in hopes that they'll run the programs and then they to can be a distribution point. I provided an example to the left that shows an IRC trojan that I believe takes advantage of a vulnerability in Internet Explorer when double clicked. The link itself appears to be a text file, but it isn't. If you are curious what it does, it reboots your computer and injects a script into your mIRC. Since that person was infected his mIRC chat client began spamming a link to infect others. To defend against these types of problems you should keep your software up-to-date (including your chat clients). And you should always look at posted links with a bit of skepticism. Be wary of sites linking to offshore web pages (in this case it is a .DE, or Germany). The link also didn't make sense in context of what we were talking about, and the link was repeated. All signs that should make you at least ask the person what it is. The fourth common way to be infected is by clicking on a link that directs you to malware. The link could either run a program and install the malware, or make use of a vulnerability that allows it to execute itself. This problem exists because the links often come from people you know and trust, and the links are often disguised with something to convince you it's harmless. All the instant messaging programs have had this problem such as AIM or Yahoo, but most of these trojans / worms occur on Internet Relay Chat (IRC). Due to the scripting engine of mIRC there are IRC trojans that take on worm like behaviors through macro virus like scripts. This allows the malware to take control of your chat client and then tell people to click on a link or such. Related to this problem, often the trojans will begin to send infected files to people in hopes that they'll run the programs and then they to can be a distribution point. I provided an example to the left that shows an IRC trojan that I believe takes advantage of a vulnerability in Internet Explorer when double clicked. The link itself appears to be a text file, but it isn't. If you are curious what it does, it reboots your computer and injects a script into your mIRC. Since that person was infected his mIRC chat client began spamming a link to infect others. To defend against these types of problems you should keep your software up-to-date (including your chat clients). And you should always look at posted links with a bit of skepticism. Be wary of sites linking to offshore web pages (in this case it is a .DE, or Germany). The link also didn't make sense in context of what we were talking about, and the link was repeated. All signs that should make you at least ask the person what it is.
Return to top.
Software Vulnerability
The fifth common infection method occurs through a vulnerability in a software application (or possibly hardware, although this is far less frequent). This problem has grown in the last few years, and I expect that this issue will become even more complex and problematic in the years to come. There are generally three types of vulnerabilities that allow them to infect you. The first is a buffer overflow, the second is improper code execution and the third is just a generic loophole. Overall these problems are not that big of a deal if you have a supported application and the software is still being developed. If you are using an outdated piece of software (such as Windows 95) or something unsupported (such as Tru64) then if a flaw is discovered then it is much harder to fix the problem. If you are running supported software then simply download and install patches from the developers in a timely fashion. In the case of Microsoft use Windows Update for Windows and Office Update for Microsoft Office.
Software Vulnerability: Buffer Overflow
A buffer overflow is a complex issue that is easily and accidentally created by a programmer. The basic concept is that a program must interact with other programs. But, the problem is that each program handles data at different rates. This creates the need for what is called a buffer, which is a technique used to regulate the data rate from one device to another device. So the program receiving the data can tell the program sending the data either to speed up or slow down depending on how full the buffer is. The buffer itself is a queue. In computer terms a buffer is a contiguous block of memory that holds the same type of data (the same type; int, float, etc.) that is divided into three segments (text, data and stack). What a buffer overflow does is feed data to a buffer passed its boundaries. Since memory is contiguous, this basically means that after a buffer has overflowed it is overwriting data of another segment of memory that is assigned to another function, or perhaps to another program altogether. The fix for this is simple, the programmer only need to make sure that the data being fed in does not go passed the bounds of the buffer, but this is often missed due to human error (if you saw the code you'd understand why). Due to the design of memory this creates a huge security risk. Contained within that memory region is also the memory address to return to when completed (computers are instructional and jump from memory region to memory region), and this area of memory follows the data of the buffer.
If a person wrote a program that fed a buffer a piece of code that overflowed the buffer, and then ended the data with a return call to the buffer, the computer would then execute the memory in the buffer space as an application and that would give the code execution the privileges of the program executing that code. And this problem is only increased when you realize software to software communication can occur over a network, just as much as on a local machine. So, not only could malware elevate its privileges if you ran it under a user account, but it could also install itself on your computer over a network if something like your network software were vulnerable. This is exactly what happened with the MSBlast worm. It affected the network abilities of Windows over a network through something called an RPC flaw. RPC stands for remote procedure call and allows your user account to interact with the Windows subsystems, and also allows remote computers to interact with Windows subsystems. Only Windows NT (NT4, 2000 and XP) operating systems were affected because Windows 9x (95, 98, Me) didn't have any RPC mechanisms, because they were designed for corporate uses. This problem can exist in any application, and even software firewalls that should protect you from this sort of thing can and do have these problems. A malware application that takes advantage of these types of flaws can spread very quickly.
For a very technical explanation of buffer overflows read, "Smashing the Stack For Fun and Profit" by BugTraq, r00t, and Underground.Org. It explains the process of buffer overflowing from a C programming perspective. I provide this as an educational document though, so don't use it for the dark side.
Software Vulnerability: Improper Code Execution
The second type of vulnerability is improper code execution. The basic concept of this is that a program interprets a piece of data as a command and executes it, when it shouldn't. This problem appears a lot in web browsers, and since email clients rely on the web browser engines they too experience these flaws frequently. By using a symbol or a command in a way not meant by the creator of the rendering / scripting engines, the program could be tricked into running a piece of code that it normally would not. A lot of times the code executed somehow tricked the program into thinking the code was from a trusted source. The outcome of these problems are that by viewing this code that takes advantage of such an issue in a program you could be infected without any confirmation. A classic example of this is with Outlook or Outlook Express. Since these email clients relied on Internet Explorer for their email viewing, if viewing a properly formatted HTML email with specific Active X commands the email could execute an attachment of the email with only the user having to view the email. This is exactly how the CodeRed worm spread. It used HTML scripting to execute an attachment by tricking the email program into thinking the attachment and the email were from a trusted zone, namely Outlook and Outlook Express believed the email was being executed from a local machine (using HTML/Active X to write applications, much like how Windows Update works) rather than from an untrusted email.
Software Vulnerability: Software Loopholes
The third vulnerability issue appears because of software loopholes. These are made from a programmer not anticipating a certain behavior of the system / user. This concept overlaps somewhat with both improper code execution and buffer overflows, but stands on its own because this encompasses bugs. Luckily this isn't normally how malware is installed. But, an example (made up) would be on a locked down Windows XP machine where the user is logged in as a guest. Normally a guest user could not modify system files, but say due to a bug the user could copy a file to a system startup folder if they did it from a third party file management tool (such as Total Commander) instead of Windows Explorer.
Return to top.
Windows File Shares
A method that many worms use to infect computers involves Windows file shares. I would like to mention that when I say Windows file shares I do not mean files share through Peer to Peer (P2P) programs like KaZaA or eMule. Instead a Windows file share is a directory/folder on your computer that others can access remotely through some type of physical network. That network could be your home network with only a few computers attached to eachother, or the Internet. This functionality is built into every version of Windows (and even DOS can be used to Windows file share).
There are two normal methods that the worms use to infect you through file shares. The first is by dropping a file in a directory that the worm programmer hopes you will notice and execute yourself. By giving it an interesting name they hope you'll run it and infect yourself. The second way is that it drops the file in a directory/folder that is either a startup folder, or uses some other means to have the file automatically executed. The automatic execution method could either be delayed (such as on next reboot) or take effect instantaneously.
By default Windows NT (NT4, 2000, XP) based operating systems share out your entire hard-drive to properly authenticated users, with the exception of Windows XP Home since it's designed for a home user. Properly authenticated users means users that can access the shares and have the proper username/password combination. In this case the properly authenticated user is most likely a program that scans your computers for weak passwords, and by weak passwords I mean passwords that are short or easily guessed. If a user has a blank password then this could potentially be a huge security risk on an open network, although it should be noted that Windows XP limits network access to your computer to accounts with passwords (meaning, by default on Windows XP an account with no password cannot be authenticated with remotely).
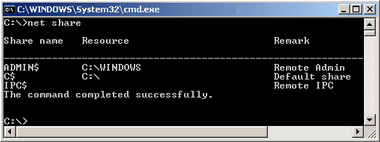 These shares on Windows NT are called administrator shares. You can tell if they are enabled by dropping to a command prompt (click on the start menu, then select run, and type in command and press the ok button). From the command prompt type in net share and you should get a response much like to the left. All shares will be returned by this. Shares with dollar signs ($) after their names are hidden shares (which means you can't browse to them, you have to know their names to reach them), and normally these hidden shares are administrator shares. The administrator shares are drive letters followed by the hidden identifier ($), as well as admin$ that shares out your Windows directory. If you see these you will want to disable them as they're a potential security risk. Run this file to get rid of them. And you will need to reboot for these shares to disappear after executing that file. These are designed for administrators on corporate networks so they can maintain a network of computers remotely. Worms that take advantage of this usually drop files in your start menu's startup folder, in your Windows folders, or somewhere that you'll notice them, such as your desktop. These shares on Windows NT are called administrator shares. You can tell if they are enabled by dropping to a command prompt (click on the start menu, then select run, and type in command and press the ok button). From the command prompt type in net share and you should get a response much like to the left. All shares will be returned by this. Shares with dollar signs ($) after their names are hidden shares (which means you can't browse to them, you have to know their names to reach them), and normally these hidden shares are administrator shares. The administrator shares are drive letters followed by the hidden identifier ($), as well as admin$ that shares out your Windows directory. If you see these you will want to disable them as they're a potential security risk. Run this file to get rid of them. And you will need to reboot for these shares to disappear after executing that file. These are designed for administrators on corporate networks so they can maintain a network of computers remotely. Worms that take advantage of this usually drop files in your start menu's startup folder, in your Windows folders, or somewhere that you'll notice them, such as your desktop.
For more information on file share security please read the security section in the Windows Setup guide.
Return to top.
|
|