|
|
Malware Guide: Detection and Removal < [5/7] >
Table of Contents
Introduction
Like any other programs malware follows the rules of any other program. In order for you to be infected there must be a program executable that is executed in some fashion. For the malware to be useful it must be set to start automatically on your computer's boot, and it must do that like any other program. Or, at least the malware must be injected into a program that it figures you'll run often. The reason being that if the malware isn't running, then it can't do anything. Next, when the malware is running it must consume memory, both on your hard-drive and in RAM. And last is that the program must be removable, although it may be a pain depending on how sophisticated the malware is.
Return to top.
Start Menu
The first place to check for malware are in your start menu startup locations. There's several of these, but they haven't changed in years so once you learn the trick then you're set for a while. The first place we should check is your startup folder on your start menu. This location can be changed, and the location depends on your Windows version, your Windows language version, and whether you've changed it. On Windows 9x (95, 98, Me) you should only have one startup folder. Normally this will be located in C:\windows\start menu\programs\start up. On Windows NT (NT4, 2000, XP) this will be located in your profile directory, as well as the all users profile. For Windows NT your profile root is located in c:\winnt\profile by default. In 2000 and XP it is located in C:\documents and settings by default. Then under that profile root there will be directories for the default user, all users and one for every user on the computer. The all users is a common profile for all accounts. So you will need to look under the all users as well as your user account under start menu\programs\startup. On Windows XP this path would look something like c:\documents and settings\john doe\start menu\programs\start up and c:\documents and settings\all users\start menu\programs\start up.
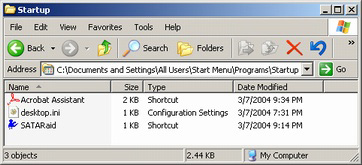 In these directories will be programs or shortcuts to programs that will execute upon logging into the computer. If your computer has no login process then it happens at the point right before your desktop icons appear on your desktop. Any of the items in the start up folder that you don't want to start by default should be removed from those directories, or deleted if you like. You should feel pretty safe removing any of the items in the start up folder because no version of Windows places any system file in these directories, so you will not be able to harm Windows itself by removing items from these folders. However, it may cause odd behavior in other programs such as Adobe Acrobat, but nothing serious. In the picture to the left you will see the items that I have set to auto startup on my Windows XP Professional computer. In case you're wondering, the desktop.ini file is a Windows resource file that is placed in every directory that gives personalized settings to that folder. Even if you see this file in a startup folder it will not run on startup. In fact, you can safely delete these files if you want, at the cost of losing personalized settings in a directory. In these directories will be programs or shortcuts to programs that will execute upon logging into the computer. If your computer has no login process then it happens at the point right before your desktop icons appear on your desktop. Any of the items in the start up folder that you don't want to start by default should be removed from those directories, or deleted if you like. You should feel pretty safe removing any of the items in the start up folder because no version of Windows places any system file in these directories, so you will not be able to harm Windows itself by removing items from these folders. However, it may cause odd behavior in other programs such as Adobe Acrobat, but nothing serious. In the picture to the left you will see the items that I have set to auto startup on my Windows XP Professional computer. In case you're wondering, the desktop.ini file is a Windows resource file that is placed in every directory that gives personalized settings to that folder. Even if you see this file in a startup folder it will not run on startup. In fact, you can safely delete these files if you want, at the cost of losing personalized settings in a directory.
Return to top.
Registry
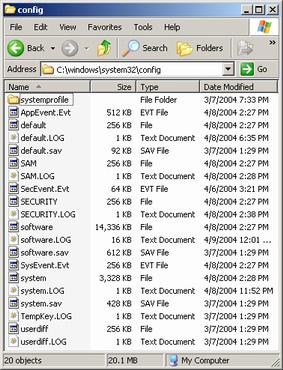 The second place to check for malware is in the registry's startup locations. If you aren't familiar with the registry then I may suggest reading my Windows Component guide on the registry. To put a little fear of God in you, the Windows registry is the central settings repository for Windows and all Windows applications. So if you edit something wrong it has the potential of corrupting your Windows installation. However, for the things we will be altering you have no chance of damaging your Windows installation, unless you make a huge mistake. The registry has been around since Windows 95 (unless you considered the REGISTRY.DAT file from versions previous to that), and now most programs take advantage of it. Since it is the settings core of Windows itself, most system functions reside in the registry. And in fact the primary location for startup files exists in the registry. This means that in the registry there are programs specified to start when Windows boots. For a quick run through the registry is composed of two main branches. The first is called the HKEY_CURRENT_USER and the second is the HKEY_LOCAL_MACHINE. In case you're wondering, the H in HKEY stands for handle (meaning that it's the controller of the key). The CURRENT_USER settings apply to the currently logged in user (or in the sake of single login operating systems such as Windows 9x, it only has a single CURRENT_USER key) and the LOCAL_MACHINE applies to all users. In reality the CURRENT_USER settings are stored in a binary database called USER.DAT in the Windows folder for Windows 9x or in NTUSER.DAT in the user's profile directory for Windows NT. The LOCAL_MACHINE settings are stored in a binary database file too. In Windows 9x it is stored in SYSTEM.DAT in the Windows folder. But, in Windows NT the hive is broken up into multiple parts in the %SystemRoot%\system32\config directory (where %SystemRoot% is a variable for the Windows folder). The second place to check for malware is in the registry's startup locations. If you aren't familiar with the registry then I may suggest reading my Windows Component guide on the registry. To put a little fear of God in you, the Windows registry is the central settings repository for Windows and all Windows applications. So if you edit something wrong it has the potential of corrupting your Windows installation. However, for the things we will be altering you have no chance of damaging your Windows installation, unless you make a huge mistake. The registry has been around since Windows 95 (unless you considered the REGISTRY.DAT file from versions previous to that), and now most programs take advantage of it. Since it is the settings core of Windows itself, most system functions reside in the registry. And in fact the primary location for startup files exists in the registry. This means that in the registry there are programs specified to start when Windows boots. For a quick run through the registry is composed of two main branches. The first is called the HKEY_CURRENT_USER and the second is the HKEY_LOCAL_MACHINE. In case you're wondering, the H in HKEY stands for handle (meaning that it's the controller of the key). The CURRENT_USER settings apply to the currently logged in user (or in the sake of single login operating systems such as Windows 9x, it only has a single CURRENT_USER key) and the LOCAL_MACHINE applies to all users. In reality the CURRENT_USER settings are stored in a binary database called USER.DAT in the Windows folder for Windows 9x or in NTUSER.DAT in the user's profile directory for Windows NT. The LOCAL_MACHINE settings are stored in a binary database file too. In Windows 9x it is stored in SYSTEM.DAT in the Windows folder. But, in Windows NT the hive is broken up into multiple parts in the %SystemRoot%\system32\config directory (where %SystemRoot% is a variable for the Windows folder).
To access the registry we make use of a program included with Windows called the Registry Editor. This is a program that view the active registry hives, allows to edit them, allows you to make security changes in Windows NT, and allows you to open external hives in Windows NT. To access the registry use the Windows registry editor (start menu, run, regedit, okay). The registry hives that we are interested in, LOCAL_MACHINE and CURRENT_USER appear identical in form of structure. Under the main hives are nested folders. The first folder under the main branches called Software contains most of the settings for applications, including Windows itself. It is under here where most registry alterations are made, at least manually through this program. In the registry there are a few terms you should know. Registry keys are folders, registry values are files and registry data are the contents of the values. There are five forms of registry values. There are strings, binary, dword, multi-string and expandable string values. From your perspective the difference is that strings contain text, binary values contain a set of numbers and dwords contain numbers up to the decimal value of 4294967295. Then multi-strings and expandable strings are just advanced strings, the difference of which is outside the focus of this guide (once again, see the Windows Component guide on the registry if you're interested in more on this).
Registry: Common Registry Startup Locations
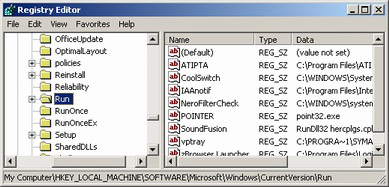 But, the first path we are interested in is found in HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion and HKEY_CURRENT_USER\Microsoft\Windows\CurrentVersion. There are multiple useful keys (remember, a key is a folder) under the CurrentVersion key that are used for startup. They are Run, RunOnce, RunOnceEx, RunServices, RunServicesOnce. If a particular key does not exist then it means you either can't see it due to permission problems (not likely in this case) or that it doesn't exist, in which case it is irrelevant. Run and RunServices both execute on startup when the user has just logged in. RunOnce and RunServicesOnce execute one startup, but the items from those lists are removed after they're executed. RunOnceEx operates the same way as RunOnce with respect to being removed after first use, but it differs that it requires a subkey and that it halts all other executions until the process completes (terminates). This is most likely by Windows updates and other patchers. Most malware will be place itself in the LOCAL_MACHINE branch over the CURRENT_USER branch because HKLM has higher authority (since it executes before HKCU and exists for all user accounts), however this could be a issue if the current user doesn't have authority to add items to HKLM. So, many malware will add themselves to both the HKLM and HKCU branches under the startup keys, many times to all of the startup keys under each respective branch. This is often a tip that the program is bad. If the program seems desperate to start then it most likely isn't good. The syntax for all of these (except RunOnceEx, which if you want more information on you'll need to see my Windows Component registry section) are the same. The value name is a text identifier, the type is REG_SZ (string) and the data is the path to the executable along with any command line arguments (also called command line parameters, they are commands given to programs at execution after the program's executable name). But, the first path we are interested in is found in HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion and HKEY_CURRENT_USER\Microsoft\Windows\CurrentVersion. There are multiple useful keys (remember, a key is a folder) under the CurrentVersion key that are used for startup. They are Run, RunOnce, RunOnceEx, RunServices, RunServicesOnce. If a particular key does not exist then it means you either can't see it due to permission problems (not likely in this case) or that it doesn't exist, in which case it is irrelevant. Run and RunServices both execute on startup when the user has just logged in. RunOnce and RunServicesOnce execute one startup, but the items from those lists are removed after they're executed. RunOnceEx operates the same way as RunOnce with respect to being removed after first use, but it differs that it requires a subkey and that it halts all other executions until the process completes (terminates). This is most likely by Windows updates and other patchers. Most malware will be place itself in the LOCAL_MACHINE branch over the CURRENT_USER branch because HKLM has higher authority (since it executes before HKCU and exists for all user accounts), however this could be a issue if the current user doesn't have authority to add items to HKLM. So, many malware will add themselves to both the HKLM and HKCU branches under the startup keys, many times to all of the startup keys under each respective branch. This is often a tip that the program is bad. If the program seems desperate to start then it most likely isn't good. The syntax for all of these (except RunOnceEx, which if you want more information on you'll need to see my Windows Component registry section) are the same. The value name is a text identifier, the type is REG_SZ (string) and the data is the path to the executable along with any command line arguments (also called command line parameters, they are commands given to programs at execution after the program's executable name).
To put you at ease here I will tell you a secret. No value in any of the startup lists is critical to Windows operation, although I would recommend not editing these lists when a critical update reboot is pending as that could cause problems since Windows does place system files in RunOnce or RunServicesOnce often when a patch is applied. Otherwise, removing any of these files should not damage Windows, although it may cause a program to operate oddly or not at all, such as a virus scanner. Therefore it is generally a good idea to backup your registry startup files before removing anything. This can be done from file, export. It will export the settings to a file that you can later run and reimport by double clicking on the backup file (or file, import from within regedit) if it happens to cause a program to malfunction that you desire (or you could uninstall and then reinstall that program to fix it if you can't distinguish the malware from the good programs).
Sometimes the name of the value can be helpful in identifying what the program is, but often the companies don't bother to give an intelligible name and you may need to look it up. Be careful though; many malware programs will try to look like a system component in hopes that you'll think they're necessary system files, rather than insidious malware. Generally I am weary of any program with a command line parameter that looks like "-hide" (since it shows that it's a program that wasn't designed for startup uses, which could be hidden trojans) or programs that don't include their path name but just the executable name (such as "point32.exe" there, but in this case it's my mouse helper application that lets me use my side buttons on my Microsoft mouse). If you can't identify a program by the name alone, or to further inspect a startup item, it is a good idea to examine the data that provides the path. From there you can identify where the file is located, and usually if a program is within an application's folder it can be trusted. Once again, be weary of programs that don't include paths because that means they're in your path (this is a term used to identify understood directories/folders, locations that are searched automatically and usually consist of Windows system folders). Most of the time malware will exist in your Windows folder, your Windows' system folder, or in your Windows system32 folder. But, the less evil ones can often be found in your Program Files folder or in your Program Files\Common Files folder. This part takes a bit of intuition, and often a bit of research to identify certain components. But, the more you do it the better you will get at it. When you want to remove a value, select it and simply use the delete key on your keyboard (that's my favorite way at least).
Registry: Infrequently Used Registry Startup Locations
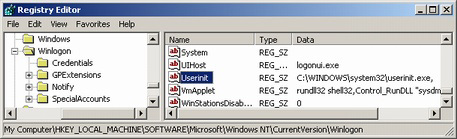 There are several other locations in the registry that are used for startup, but luckily they are very similar in nature. However, it should be noted that these locations are very infrequently used. The next location type is found in HKLM\Software\Microsoft\WIndows NT\CurrentVersion\Winlogon. And there are three types of startups you should be interested in here. There are several other locations in the registry that are used for startup, but luckily they are very similar in nature. However, it should be noted that these locations are very infrequently used. The next location type is found in HKLM\Software\Microsoft\WIndows NT\CurrentVersion\Winlogon. And there are three types of startups you should be interested in here.
The first is located in a value called Userinit. It's a string (REG_SZ) and contains a list of items that are started when a user logs in. Multiple items can be added to this value by using commas ("userinit.exe", "worm.exe", "trojan.exe"). Normally this is used by userinit.exe that is a process that begins when a user logs in and then exists after it completes the login process. This application runs login scripts used in group policies and starts the network shell. I have never seen any worm or trojan make use of this startup location. But, that does not mean it hasn't been used and I guess it will be if it has not been. The second is a string value called Shell. Like the Userinit it is executed after logging in. However, the file listed in the shell value is executed after and by the program listed in the Userinit string.
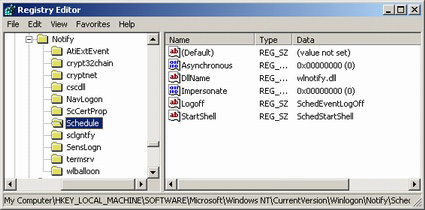 Also, there are subkeys to the Winlogon key that are of interest. If you browse to this in your registry you will notice several keys under Notify. Under each of these keys you will see a string value called DllName that names a DLL. If you are not sure what a DLL is then the concept is very easy. A DLL is a special form of an executable that can only be triggered as a command line parameter to rundll32 (like, "rundll32 cscdll.dll"). DLLs are shared resource executables that programs jointly use to take advantage of a centralized tool. This section is not often used by malware, but I have seen a few malware applications (like a very insidious spyware/adware program called ZestyFind use this section to startup). The picture shows you the subkeys that I have in Windows XP, and I would assume others are unnessarily added in by 3rd party programs. If you delete one of these keys (folder) then it will no longer load the DllName anymore. Just be careful that you research the thing you're deleting before you go and do it. Deleting one of these could have potential harmful results if you delete something important. Also, there are subkeys to the Winlogon key that are of interest. If you browse to this in your registry you will notice several keys under Notify. Under each of these keys you will see a string value called DllName that names a DLL. If you are not sure what a DLL is then the concept is very easy. A DLL is a special form of an executable that can only be triggered as a command line parameter to rundll32 (like, "rundll32 cscdll.dll"). DLLs are shared resource executables that programs jointly use to take advantage of a centralized tool. This section is not often used by malware, but I have seen a few malware applications (like a very insidious spyware/adware program called ZestyFind use this section to startup). The picture shows you the subkeys that I have in Windows XP, and I would assume others are unnessarily added in by 3rd party programs. If you delete one of these keys (folder) then it will no longer load the DllName anymore. Just be careful that you research the thing you're deleting before you go and do it. Deleting one of these could have potential harmful results if you delete something important.
Registry: All Registry Startup Locations
I realize there are a lot of places to memory where items can startup in the list, but below I have provided a table of all true startup locations in the registry. Since there are so many I have ordered them with respect to how often malware take advantage of them.
Key |
Value |
Description |
Software\Microsoft\Windows\CurrentVersion\Run
Software\Microsoft\Windows\CurrentVersion\RunOnce
Software\Microsoft\Windows\CurrentVersion\RunOnceEx
Software\Microsoft\Windows\CurrentVersion\RunServices
Software\Microsoft\Windows\CurrentVersion\RunServicesOnce |
{string} |
These exist in both the CU and LM hives and are loaded on login. The value name identifies the startup item, but the name can be any allowable value name. The value is of type string (REG_SZ) and the data contains the filename to the executable, but can also include the path. |
Software\Microsoft\Windows\CurrentVersion\RunServicesOnce\Setup |
{string} |
This only exists in the CU hive. A progress dialog box shows up and displays the progress of the execution of each item in this list. As ma |
Software\Microsoft\Windows\CurrentVersion\Policies\Explorer |
Run |
This exists in both the CU and LM hives. They are applied normally by group policies. |
Software\Microsoft\Windows NT\CurrentVersion\Winlogin |
userinit |
This is a LM only key. This processes a list of comma separated executables. By default this should contain userinit.exe. |
Software\Microsoft\Windows NT\CurrentVersion\Winlogin |
Shell |
This is a LM only key. This specifies the executable userinit should start during the login process. By default this is explorer.exe. |
Software\Microsoft\Windows NT\CurrentVersion\Winlogin\Notify\{string} |
DllName |
This is a LM only key. Under the notify key there can be keys that load a specific DLL from the DllName value. |
Software\Microsoft\Windows NT\CurrentVersion\Windows |
load |
This is a CU only key. I believe this only executes a single filename. |
Software\Microsoft\Windows NT\CurrentVersion |
ShellServiceObjectDelayLoad |
This is a LM only key. The values listed under this key are started as a part of Windows. Normally the data for the values list CLSIDs instead of an actual executable. |
Return to top.
Services
The third place to check for malware is a component of Windows that exists only in Windows NT (NT4, 2000, XP). If you are using Windows 9x (95, 98, Me) then this section does not pertain to your operating system version. If you are interested in a comprehensive explanation of Windows services then I recommend reading my guide on Windows Components.
The services are a special form of startup items (in Unix these would be called daemons instead of services). Windows NT was designed as a workstation/server operating system so that it could operate well on corporate networks, where there exists normal users and an IT administrative group. The major division between Windows NT and Windows 9x is that multiple user abilities exist (normal users that have limited access and administrators that had full control). Also the components of Windows were more clearly separated and modularized, allowing a system administrator to pick and choose the abilities of the workstation/server. Therefore a feature of Windows was created called services. These are startup items that execute before the login process on the computer occurs, because specific programs (like a web server or even network control) need to be running even when no one is logged into the computer. The services not only start programs, but also kernel level system drivers.
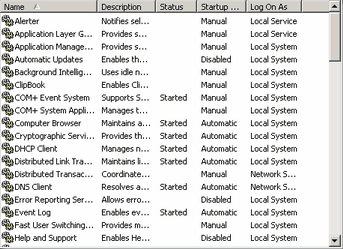 In order to modify the system services we use the Windows Services MSC (start menu, run, services.msc, okay). For more information on MSCs please see the Windows Components guide on them. The MSC for the services simply presents you with a tabulated list of information on most system services. I say most because Windows hides the most system critical services (mostly drivers). For more information on how to access those advanced features of system services please read the Windows Components guide. These services can also be malware, because any programmer is allowed to write his program to be a system service and have it load on startup. So, the ability to look through this list and identify possible malware applications is very important. In order to modify the system services we use the Windows Services MSC (start menu, run, services.msc, okay). For more information on MSCs please see the Windows Components guide on them. The MSC for the services simply presents you with a tabulated list of information on most system services. I say most because Windows hides the most system critical services (mostly drivers). For more information on how to access those advanced features of system services please read the Windows Components guide. These services can also be malware, because any programmer is allowed to write his program to be a system service and have it load on startup. So, the ability to look through this list and identify possible malware applications is very important.
By default there should be five columns; name, description, status, startup type, and log on as. The name column tells you the long name of the service (the short name is not displayed here, more about that later). The service can be named most anything, and several of the names won't be very straight forward. For example, in the picture to the left you can see a printer spooler service. That name pretty much explains what it is, it spools (intelligent queuing system) items you print. But, how about the QoS RSVP service? Well, that's a much more cryptic name. In case you wanted to know though, QoS stands for Quality of Service and is used to reserve a specific amount of bandwidth for mission critical applications (such as VoIP, running a phone through your Internet service... you'd want it to ring even when downloading). So, you can't just assume something is bad because it has a bad name. The description is often helpful in identifying what a service is when the name isn't helpful. The description, like the name, may be pretty cryptic or even blank. And of course, if it is malware then the description could be a lie, as could be the name. But, to narrow down the search you really only need to worry about applications with the status of started or the startup of automatic. Why? Well, the status shows whether that service is currently running or not. More than likely if it is malware it would be needed to be running in order to pose any threat. There are a few exceptions to this rule though as some malware will run a script that executes another process external to a system service, in which case the service is just the spawn point. But, this is where the startup type comes in. For that column you can have automatic, disabled and manual. Automatic means that program executes every time the computer starts up, and possibly every that that system is terminated (such as when it crashes). Manual means that program executes only when a different program requests it (such as if your network connection service is set to manual and you try to access the Internet, it would then start the network connection service). When set to disabled that service cannot be executed unless switched off from disabled. Therefore, you really only need to worry about automatic services, and to a much lesser extent, manual services. The log on as column shows you what type of service it is. Services can either be executed as local system, network system or under the identity of a particular username. This means that a service can either be a component of Windows (local system), a component of Windows' network infrastructure (network system) or pretend it is a particular user (network system). Most services will run as local system, and malware is no different in this respect.
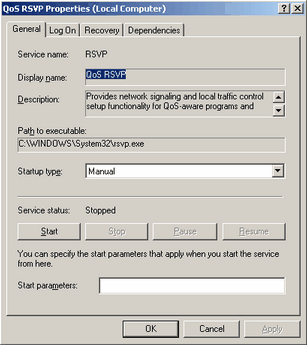 To get more information on a service double click it. This will open up a dialog box for that particular service with all the information that Windows knows about it (which isn't much, Windows just runs what it is told). From the general tab you can get the service name (this is the short name, this is the name that Windows actually identifies a service by), the display name (the long name, which is basically a short description), the description, the path to executable (this is where the program is located), the startup type, the status (whether it is running or not), and you are able to start or stop the service. Most important system services will not let you stop them because it would cause Windows to crash (you'd have to reboot, it wouldn't cause any permanent damage). And some malware is the same. To protect themselves they will pretend that they're an important system process or restart themselves right after being terminated. I haven't seen it yet but they could also just restart Windows if you attempt to stop them. If you do identify malware and you can't stop them, you could set them to disabled and reboot. This would make it sure that they can't start, but just make sure it is malware because Windows can't override that and a disabled critical system service will make Windows not startup. To get more information on a service double click it. This will open up a dialog box for that particular service with all the information that Windows knows about it (which isn't much, Windows just runs what it is told). From the general tab you can get the service name (this is the short name, this is the name that Windows actually identifies a service by), the display name (the long name, which is basically a short description), the description, the path to executable (this is where the program is located), the startup type, the status (whether it is running or not), and you are able to start or stop the service. Most important system services will not let you stop them because it would cause Windows to crash (you'd have to reboot, it wouldn't cause any permanent damage). And some malware is the same. To protect themselves they will pretend that they're an important system process or restart themselves right after being terminated. I haven't seen it yet but they could also just restart Windows if you attempt to stop them. If you do identify malware and you can't stop them, you could set them to disabled and reboot. This would make it sure that they can't start, but just make sure it is malware because Windows can't override that and a disabled critical system service will make Windows not startup.
The other tabs include some helpful data too. The log on tabs show you the access the service has. Like previously stated this can be local system, network service or a login name. Remember that a service has to be executed like any other program, and with Windows NT security permissions the only way to get access to secured files (through access control lists) is through a username that has access to the files. When a service is executed under a username it has the same security potential as that user would have. So if that service is executed under a user with guest access, then any file it tries to access that doesn't allow guests to view it the service wouldn't be able to view. The network service is a unique type of logon ability that limits a service to only modifying network configuration data. And the local system is another unique type of logon ability that trumps all theoretical security. That means that local system is above administrator and it's an unassignable access level to users, but it allows access to all computer resources. The recovery tab allows you to choose settings that identify what occurs if the service crashes. This is especially important for system services that are required for Windows to run. It can be used to restart the computer or restart the service or do nothing at all. The dependencies are the other services that this service requires the use of. If this service is started and a dependency is not it will start it if it is set to automatic or manual, if it isn't already. If the dependency is disabled or can't start then this service will not start either.
Return to top.
System INIs
An initialization configuration file, called an INI by the file extension given to it (.ini) is a plain text file (without any type of formatting such as bold or italic) that a program reads into memory when they are executed. The data contained in the text file represents settings that are unique to the program. The INI contains sections, items and values. The sections are the values contained between brackets ([ and ]). The items following a section name are the items. The text after an item's equal (=) symbol are called values. Basically items are variables that contain the value data under a group of the section. A value can be blank and that represents that the item has no data. Normally an item has to have a unique name for a section, but this isn't always the case. A section doesn't need any items at all, but that means that section is just a placeholder. If an item does not exist then it means it has no value, but that could also mean internally it has a default value that the system attributes to that item in that section.
In Windows INIs were the devices used to store configuration data before the registry was created (before Windows 95). But, the registry is a faster system to parse (since it contains binary data instead of text data), the registry has a centralized location instead of being a text file amongst hundreds or thousands of other INIs, the registry allows for security permissions that lets you choose what users can modify what INIs in what ways, and the registry allows for other programs to make use of its central data repository while an INI would be created for every program that wants to store settings. But, INIs are simplistic and able to be read in any text editor, such as notepad, while the registry requires a specific program written for the task to access the registry hives (regedit for example).
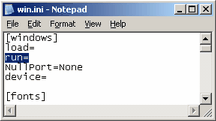 Since Windows had a history with using INI files the features provided by the INIs have been retained to allow backwards compatibility; so old programs still can function using their archaic configuration data storage methods. Back before Windows 95 (specifically in Windows 3) the two most important INI files were the win.ini and the system.ini, which were both stored in the Windows folder (most likely C:\windows). Most configuration options chosen in Windows, such as the desktop wallpaper and the drivers to make use of the computer's hardware, were stored in these files. Normally you wouldn't edit these files manually, but the fact that these were text files allowed you to easily do so if the need arose. In the picture to the left is a screenshot of a win.ini from a Windows 98 machine. You will notice that it has sections (windows, Desktop, intl), items (load, run, NullPort, device, Wallpaper, TileWallpaper, WallpaperStyle, etc.) and values (None, Corel Barista,Barista,BAR:, (none), 1, etc.). Since Windows had a history with using INI files the features provided by the INIs have been retained to allow backwards compatibility; so old programs still can function using their archaic configuration data storage methods. Back before Windows 95 (specifically in Windows 3) the two most important INI files were the win.ini and the system.ini, which were both stored in the Windows folder (most likely C:\windows). Most configuration options chosen in Windows, such as the desktop wallpaper and the drivers to make use of the computer's hardware, were stored in these files. Normally you wouldn't edit these files manually, but the fact that these were text files allowed you to easily do so if the need arose. In the picture to the left is a screenshot of a win.ini from a Windows 98 machine. You will notice that it has sections (windows, Desktop, intl), items (load, run, NullPort, device, Wallpaper, TileWallpaper, WallpaperStyle, etc.) and values (None, Corel Barista,Barista,BAR:, (none), 1, etc.).
The two items to notice here are load and run. These are the old startup locations that were later replaced by the registry startup location for Run, but this old ability still exists. These were replaced because it only allowed a single string of startup programs for every user of the computer, whereas the registry allows each user to have a list of their own startup files. Plus, this didn't distinguish between a program (Run) and a service (RunServices). The syntax of the data for the run item is the path name to the program that is to run on startup. If let blank then no program will start. If the path of the program isn't given, and just a filename is supplied then the program is executed if it is found in the system path (the path is a group of default paths to search for programs that aren't executed with a supplied path). Many malware applications will hide in this section because so few people will search for them here. Since only a program executable is given here you will have to identify the program by its name. If you cannot figure out what it is then it may be helpful to do an internet search on the program, or to locate it on your computer. Often printer drivers will place themselves here, such as the HP software suites to provide notification of when your ink is low.
Return to top.
File Associations
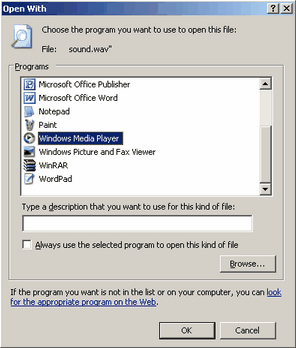 A fairly rare startup location are within file associations. File associations are the way Windows relates a data file to an application. It does this through file extensions. A file extension is a name extension that follows the period (.) character on a filename. In the registry (see above) there are entries for which programs handle what file extension, as well as contain other information such as which icon is used for what file extensions. This is the only way a Windows based program knows a text file is a text file and should be opened with notepad, or that a Word document is a Word document and should be opened with Microsoft Word. The benefit of this is that these extensions can be changed so that you can use your favorite program to open a particular file type, so you could change the behavior of text files and have them open with your favorite alternate text editor when you double click them. A fairly rare startup location are within file associations. File associations are the way Windows relates a data file to an application. It does this through file extensions. A file extension is a name extension that follows the period (.) character on a filename. In the registry (see above) there are entries for which programs handle what file extension, as well as contain other information such as which icon is used for what file extensions. This is the only way a Windows based program knows a text file is a text file and should be opened with notepad, or that a Word document is a Word document and should be opened with Microsoft Word. The benefit of this is that these extensions can be changed so that you can use your favorite program to open a particular file type, so you could change the behavior of text files and have them open with your favorite alternate text editor when you double click them.
This brings up a confusing topic for some because Windows by default hides these file extensions because Microsoft believed the concept of a file extension was confusing. They also believed that the icons should be enough information to identify the type of file, although I very much do not agree with their developers on this topic. If you are not able to see extensions on files (such as a text file ending with .txt in its name or a Word document ending with .doc or an executable ending in .exe) then you have extensions disabled. The way to disable the feature to hide the file extensions varies with each version of Windows (to complicate things). But, conceptually these options remain in the same place on every version of Windows. If you open a explorer view of any folder on your computer (for the easiest, open My Computer) there is an option to edit the options for the view of folders from a drop down (for XP it is under tools and then folder options). Under the view tab there will be an option that you must uncheck that calls itself hide extensions for known file types. Removing this feature will allow you to see the true file types of programs.
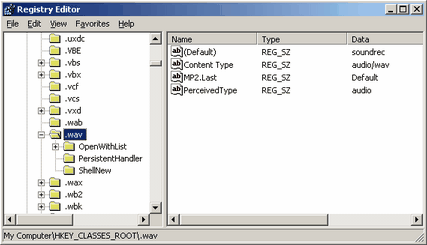 So far the concept of a filetype seems benign. However, the concept is that when you double click an application (or right click and select a task on that file) a particular associated file is executed to handle that data file. The danger here is that any installed program can associate file types to itself or other programs. This means that if you download malware, it could easily, as an example, add itself as the handler of text files, so that whenever you execute a text file that Windows would run that malware application. The problem gets messier because a few malware applications intelligently handle this, and when executed they will then start the program that in the past handled that file association, so to the user nothing out of the ordinary happens. So if you are having trouble locating how a program starts up then it is possible that it has associated itself with a file type. So far the concept of a filetype seems benign. However, the concept is that when you double click an application (or right click and select a task on that file) a particular associated file is executed to handle that data file. The danger here is that any installed program can associate file types to itself or other programs. This means that if you download malware, it could easily, as an example, add itself as the handler of text files, so that whenever you execute a text file that Windows would run that malware application. The problem gets messier because a few malware applications intelligently handle this, and when executed they will then start the program that in the past handled that file association, so to the user nothing out of the ordinary happens. So if you are having trouble locating how a program starts up then it is possible that it has associated itself with a file type.
In the registry the file types are stored in the HKEY_CLASSES_ROOT visual hive. In reality these entries are stored in HKLM\Software\Classes and HKCU\Software\Classes but also have an alias in the root view of the registry editor. The majority, and the most important, associates belong to the LOCAL_MACHINE handle. The concept here is that a file extension contains a file handler or a persistent handler that it is associated with. This usually relates back to what is called a CLSID, which is basically a long string of characters that relate programs internally. Following these chains you can locate the related application. Personally I find the internal implementation confusing so it would take a good amount of time to explain. In a later revision I will detail this procedure more, or perhaps add file types to the Windows Components guide. For the time being if you feel you need more information on this topic then I suggest searching Google for the information.
Return to top.
Task Scheduler (Scheduled Tasks)
Another execution point is your task scheduler. This is a feature of Windows that was introduced to allow scheduled execution of programs or scripts so you could, for example, set your computer to automatically defragment over night. This feature is sometimes called scheduled tasks, but that is the same thing. The basic concept is that the task scheduler is a program, as well as a service in NT based operating systems, that polls its database for configured events and executes the desired command when a trigger time arrives.
It is possible a malware application could be added as a scheduled task that executes every day to make it harder to remove it. So if you are having trouble locating the starting point for a malware application then you may want to look here. I have never seen anything use this before, besides good applications, but I have included it to be complete.
You can find the task scheduler / scheduled tasks in your start menu, normally under system tools in the accessories sub menu. If you do not have the icon then in Windows XP (and possibly previous versions) you can execute explorer.exe ::{20D04FE0-3AEA-1069-A2D8-08002B30309D}\::{21EC2020-3AEA-1069-A2DD-08002B30309D}\::{D6277990-4C6A-11CF-8D87-00AA0060F5BF} from the run menu in your start menu and it should start the task scheduler.
Return to top.
Screensaver
Another place to look for malware, if you can't find it starting elsewhere, is as your screensaver. Screensavers are just special executable programs that end with a SCR extension. It is possible that a crafty malware application could use the screensaver as a starting point. You can find this by right clicking on your desktop and selecting properties. The drop down box on the screen saver tab lets you pick your screensaver. If there's anything in there that looks suspicious then select something else as the screensaver. It should also be noted that a few freeware screensaver bundle packs come along with spyware/adware, but they are not spyware/adware themselves.
Return to top.
|
|